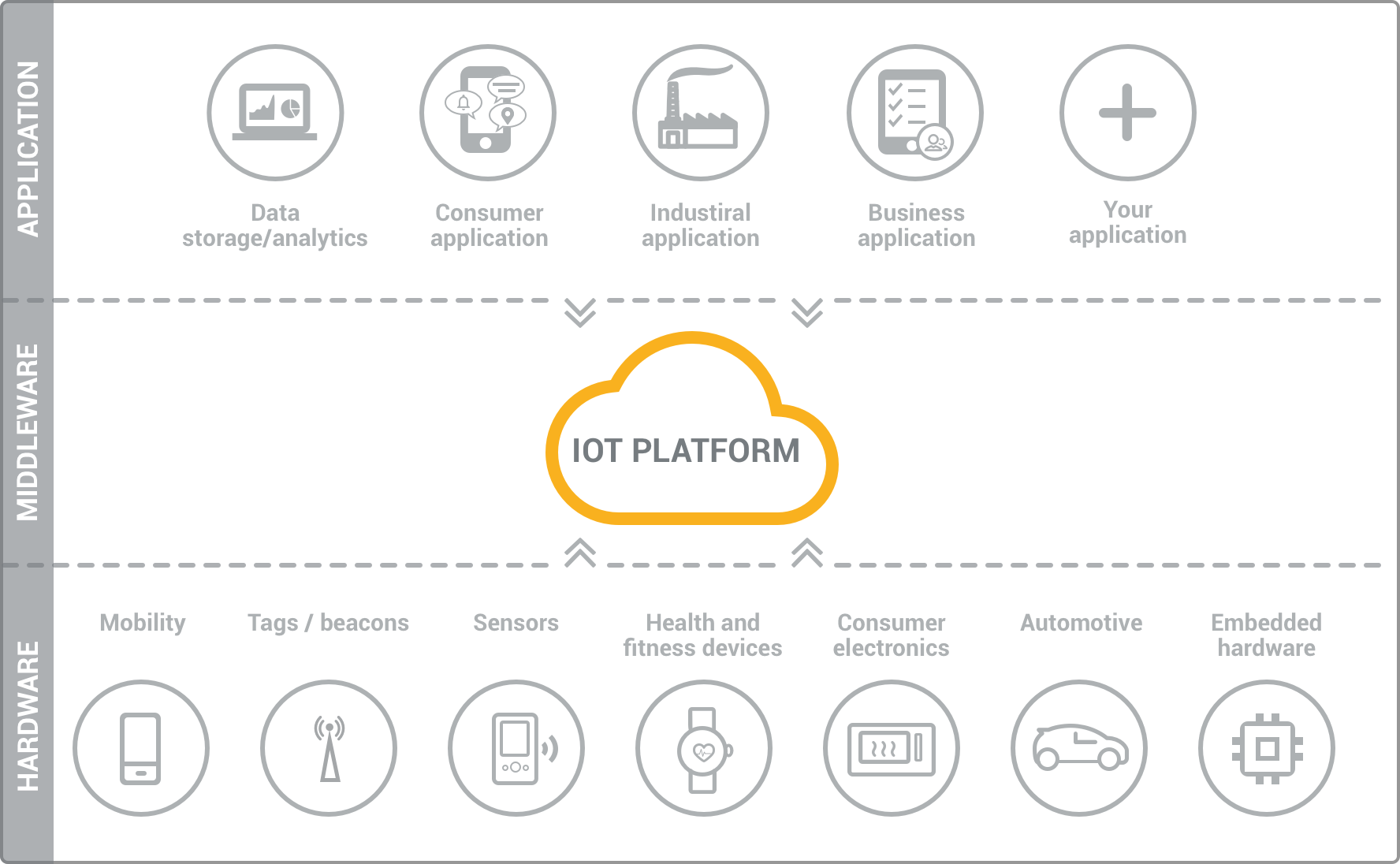
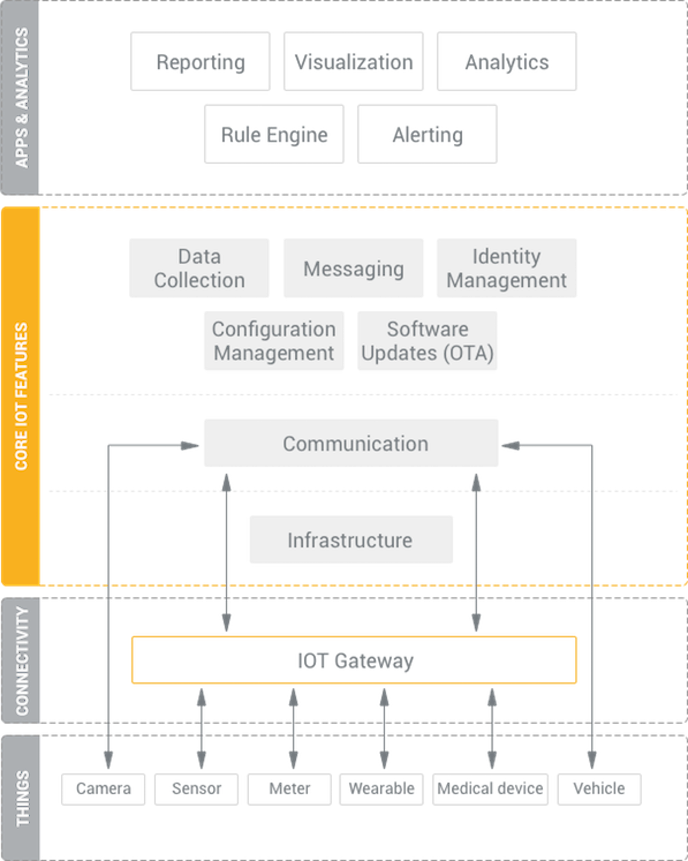
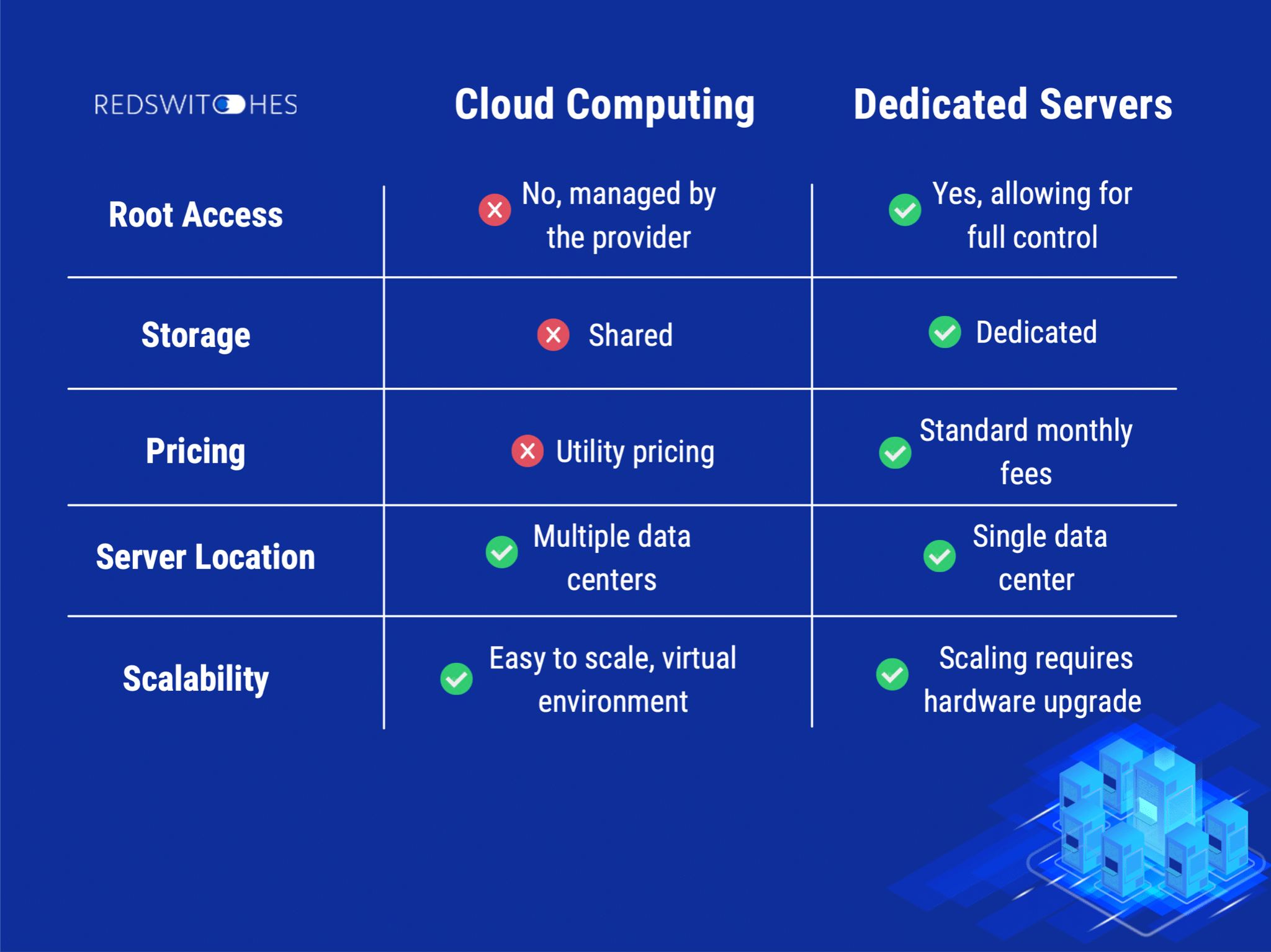
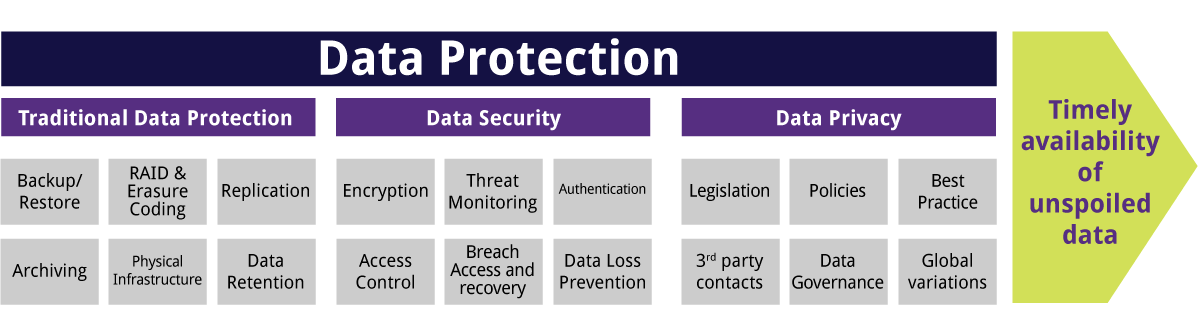
The Buzz on Server Hosting
or the staff to manage its maintenance. Just as with maintenance, assistance in a remote hosting version is basic as well as effective. Why? Because the company hosting the software application concerned is the one that looks after it. Whether it's a recently released spot that needs to be processed or a configuration concern that needs addressing, the service provider looks after it, rather than the user.
Your site has outgrown its common organizing account, and also you now require to relocate to an extra. This is something you need to celebrate, as it indicates your project is headed in the appropriate instructions. The only point you might not be certain around is the Let's have a look at and see what you'll obtain in exchange for the additional money.
Some Of Servermania
The digital web server you get with a VPS strategy gives you a for your website. It has, and, most importantly, the actions of others can not impact its performance. The allow you change the server's configuration at the click of a mouse, and you do not require to spend for hardware you do not use.
The only issue is, unskilled individuals are not sure if they can manage an entire online web server by themselves. Commonly, they're not accustomed to the, as well as they have no suggestion exactly how to carry out software setups, use safety patches, as well as take care of server upkeep tasks. With a handled VPS, you will not need to assume about any one of these points.
Your VPS host releases the and configures it so you can. They likewise take treatment of the ongoing maintenance of the server framework and all the software set up on your VPS.
The Servermania PDFs
A managed web server will certainly save you a great deal of time googling, reviewing overviews, flipping through food selections, as well as implementing commands, which is a guaranteed plus. Yet what are the other benefits that can directly influence your site's efficiency and your total experience? The more CPU cores, memory, and disk area you have, the much faster your site is.

They are offered around the clock, and also they have the knowledge to recognize as well as before they can cause too much damage. VPSs are produced through. Throughout it, a part of a physical web server's hardware sources are assigned to a digital equipment, as well as they stay scheduled for this equipment just.
The Main Principles Of Servermania
On the other, you can easily include added whenever you need to. You do not also require to reboot the digital maker to finish an upgrade. With a taken care of VPS remedy, you can normally take benefit of that reveal you specifically what sort of web server sources you're utilizing at any offered time.
On a shared server, numerous accounts use the very same equipment resources (ServerMania). If simply among the web sites experiences a major web traffic spike, the efficiency of the entire web server may be compromised, affecting the rest of the jobs hosted on the device. With a virtual private web server, this isn't a trouble.
This implies that it requires to be. Safety needs to be. At Scala, Hosting, as an example, we've put all our experience as well as expertise into creating custom services tailored to our managed VPS platforms. Every handled web server benefits from real-time tracking, and also it features specialized devices designed to, secure you from spam, as well as guard you from many other risks.
See This Report about Server Company
If you have a self-managed web server, you will be in charge of establishing a backup solution and also configuring it. You need to decide exactly how regular your back-ups must be, and also you additionally need to think of how you store your back-ups. This may imply hiring an additional server simply for your back-ups.
Your back-ups and pictures are totally automated, and also, ideally, they're saved on a remote web server suggesting a working duplicate of your website is easily obtainable any time. Your managed VPS needs to be equipped with a center for, as well, as well as if you're having a hard time, you can constantly ask your host's support group to direct you in the explanation right instructions.
The number of cyberattacks right here has expanded quite a bit over the years, as well as the volume of delicate info we share with sites is significant. Now, if you do not have an SSL certificate, the majority of modern browsers will certainly flag your web site as, and you'll likewise have actually a.
Excitement About Server Company
Bear in mind, however, that managed solutions are furnished with numerous devices that can be crucial for handling your task. Obviously,. As an example, presumably, a self-managed web server might be more affordable than the equal took care of remedy, but if you desire to make use of, you require to make up the licensing costs.